Dealing with Spam and Data-Breaches
Introduction
Most companies are doing an atrocious job when it comes to protecting their customers’ data. This starts with using outdated and vulnerable software or having default passwords on their services and ends with poor company-internal security, such as untrained employees. Some companies are not even hashing passwords before storing them in their databases, but instead store them as plain text. I would really try to avoid using these services at all, if you can help it.
And don’t be fooled, this does not only apply to smaller businesses, no. Even some of the biggest companies in the world have messed up numerous times before, resulting in massive leaks of sensitive user data, such as: emails, passwords, phone numbers and other personal information such as your address etc. A quick look at Troy Hunt’s great website Have I Been Pwned shows us a really long list of known data breaches.
And these kinds of data breaches happen all the time!
But in this blog post, let’s focus on leaked email addresses. I might cover leaked passwords etc in a future post :)
Why do you get spam?
When a company with which you have a registered account gets hacked, your email address is most likely also part of that data breach. Hackers will then compile a huge list of all the email addresses in that data breach and use them to mass-send spam/phishing emails to those email addresses.
Out of those thousands or millions of emails, one is going to arrive in your inbox, and if you are not careful, you might fall for it. All of that can happen because your email appeared in that data breach.
What to do about it?
It is important to keep in mind that once something gets leaked onto the internet, it’s going to be there forever. Hence, it is important to put some thought into what information we put up in the first place. So, what can we do about that? Luckily, there are a couple of things we can do:
- Use temporary emails for irrelevant accounts.
- Use shared accounts to access irrelevant content that requires registration.
- Use unique email aliases to protect your real email address, e.g., with SimpleLogin.
Temporary Emails
When you want to register for a service that you really don’t care about at all, and you will only use it once anyway, it might be worth trying to register with a temporary email. A temporary email is an email that gets dynamically generated and deleted after a couple of minutes. Some temporary email providers are listed below.
- https://muellmail.com/
- https://tempmailo.com/
- https://10minutemail.net/
- https://www.sharklasers.com/
Note, however, that some services blacklist temporary email providers, so it is not guaranteed that you can use them to sign up. But it is worth a try regardless.
BugMeNot
Sometimes, you might not want to register at all - you probably just want to access content on a website, but it requires an account to do so. In that case, you could try to check if http://bugmenot.com/ has an account. Those are throwaway accounts that people made for websites, that you might be able to use. I think this goes without saying, but obviously don’t use these accounts for anything important, and don’t put any personal information up on these accounts.
SimpleLogin
Now, let’s talk about the best solution that I also use every day: SimpleLogin. SimpleLogin is an open source email alias software that allows you to protect your real email address. So, instead of signing up with your real email address, you sign up with an alias you generated in SimpleLogin, - and all emails will be forwarded to your real email address, if you want to. This image explains that really well:
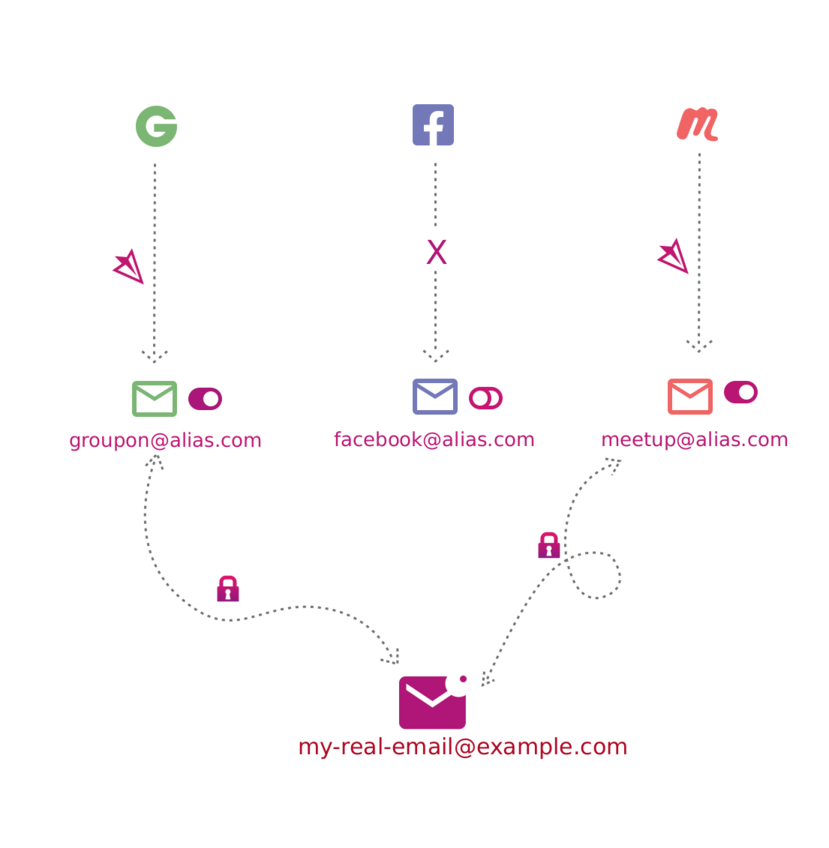
Using this approach has some massive advantages, most notably:
- Unique emails: You don’t have to use the same email address for every service you sign up with. You can create one unique alias per service. This improves your privacy a fair bit because cross-referencing your email becomes a lot harder. The service you sign up at does not know your real email address, just the alias.
- Custom Domains: You can use your own custom domains if you want to, or you can use some that SimpleLogin provides.
- Security insights: When you receive spam emails, you can see which alias is forwarding the spam emails. This makes it much easier to narrow down which service got breached and which alias got affected. All it takes is ticking a checkbox in your SimpleLogin dashboard to disable forwarding if the spam gets annoying or create a new alias for that service. No more spam in your real email inbox!
- Reply via alias: SimpleLogin can not only be used to forward emails but also to send emails. An alias is a full-fledged email address.
- Reliability: There is no risk about SimpleLogin not being a thing anymore in the future. It’s open source and can be fully self-hosted, which means you will never lose access to your aliases.
- Fine-grained control: You can also choose which alias gets forwarded to which (real) email address of yours. That way, you could, for example, separate between your work and private email.
The free plan of SimpleLogin allows for 15 aliases, and for $30/year, you can create unlimited aliases. Or, if you decide to self-host the entire thing, you can also create unlimited aliases for free.
Closing Thoughts
Obviously, I am in no way affiliated with any of these services. I just think they are great, and maybe you’ll find some use in them too. This might not fully prevent spam, but it will definitely help minimize the amount without the risk of your real email address being abused for some malicious purpose. So yeah, give it a try and see for yourself. :)